
Filesystem
Parsing
There are many tools available to read and extract the contents of most filesystems such as NTFS, FAT32, and EXT. However, our clients have run into obscure filesystems in embedded devices that cannot be analyzed or reconstructed using any commercial software. These obscure filesystems are used to provide a level of security for the manufacture and without the ability to analyze the data at a filesystem level it would be next to impossible to make sense of the data.
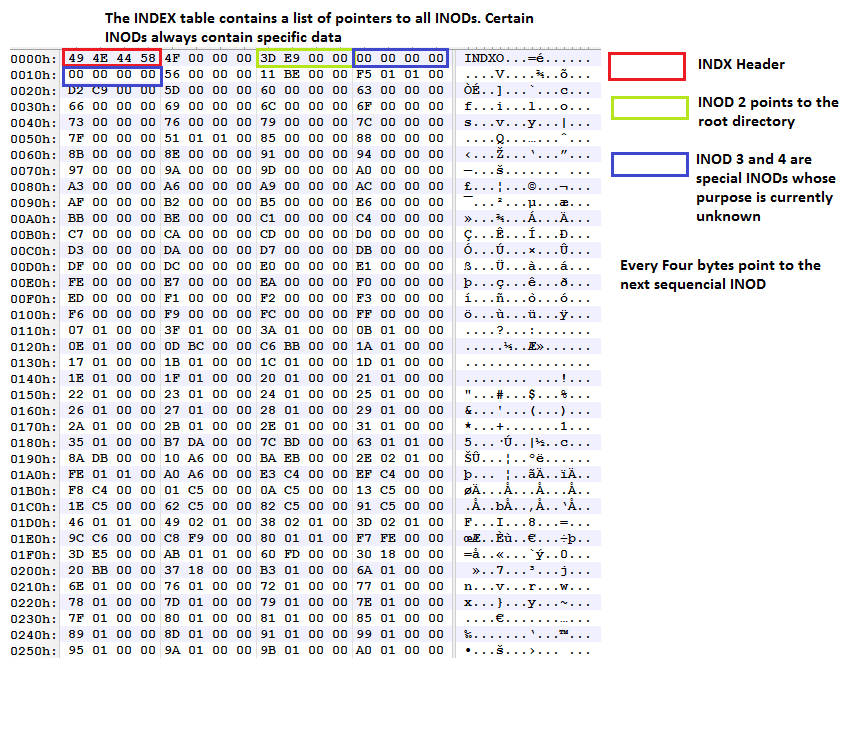
Figure 1: Most Filesystems contain a file alocation table which points to where on the disk the file resides.
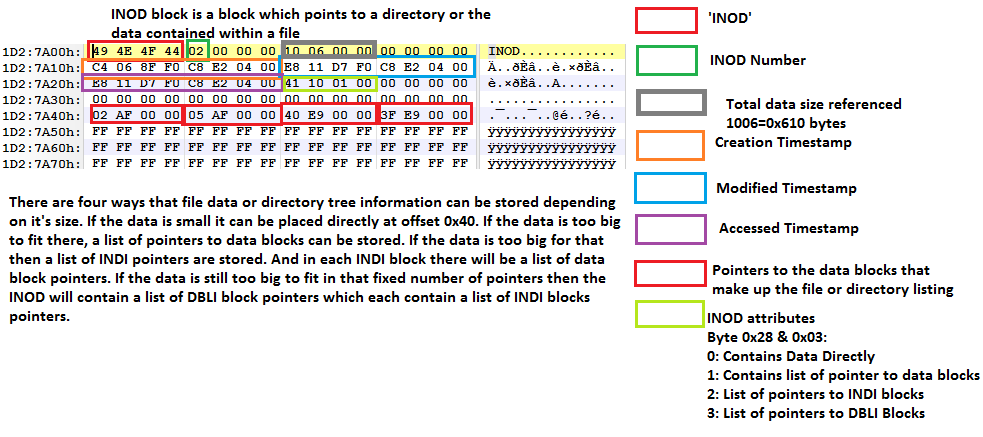
Figure 2: This Filesystem uses Inodes which contain a list of blocks where the actual filedata is stored.
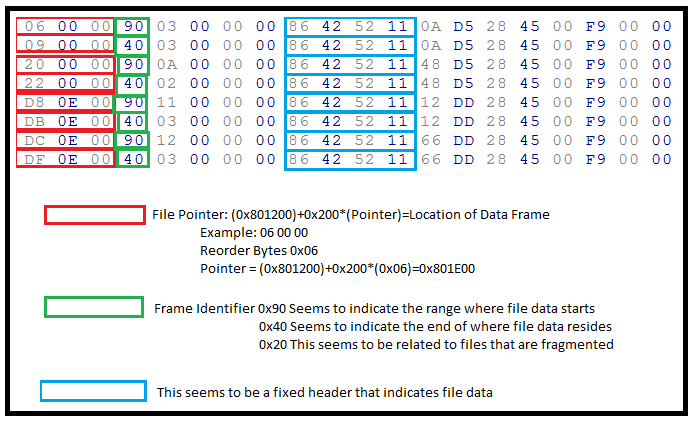
Figure 3: Files are often not stored in continous memory and are fragmented requiring tools to fetch each data block sequencially to recreate the file correctly.
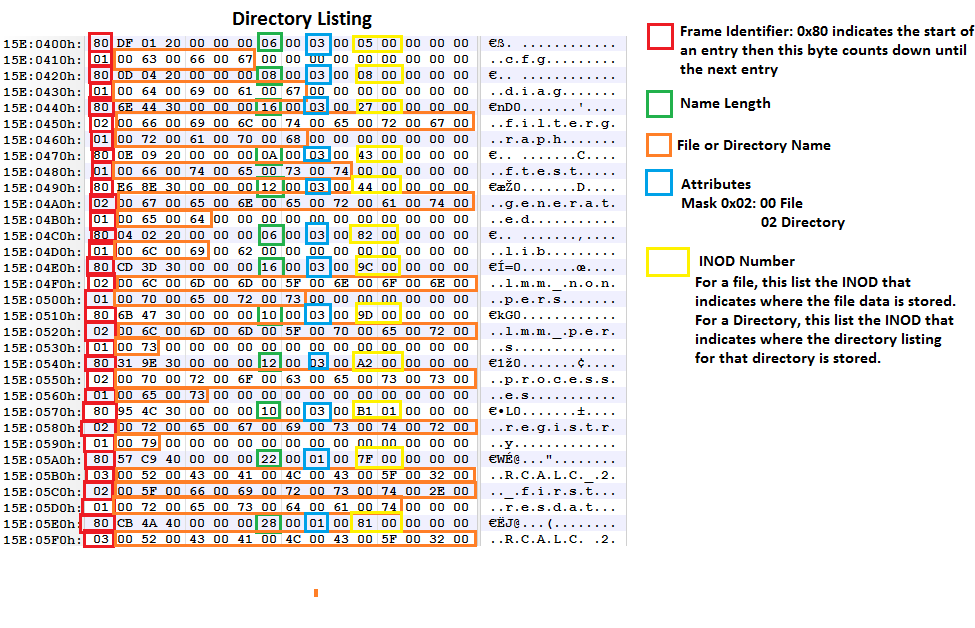
Figure 4: Directory Listings contain the pointers to the files and directories residing in that directory
At
Reverse Engineering Consultants we can reverse engineer these
filesystems and create software tools that can extract the files and
folders
and convert them into a common filesystem that can be easily analyzed.
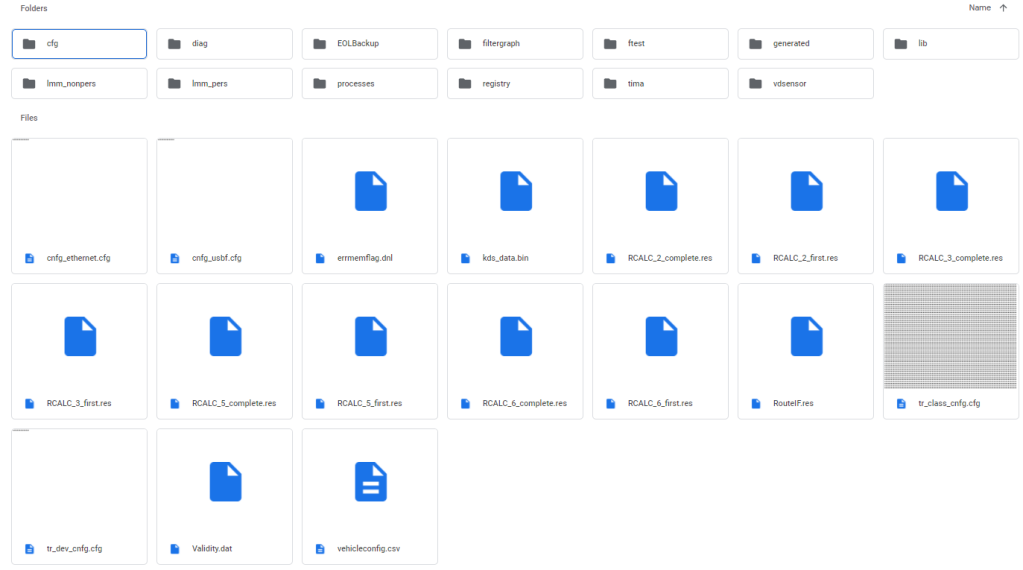
Figure 5: Once a filesytem is reverse engineered tools can be created to recreate the filesystem in Windows or Linux
As an extension of this type of reverse engineering, many flash memory chips contain a wear leveling scheme which jumbles the pages of memory rendering filesystem analysis impossible. Wear leveling is designed to protect solid state flash memory from consecutive writes on the same page because each write cycle wears out that page. By spreading out the writing on flash memory the life of that memory is extended. Data Parsing Services has experience reverse engineering these schemes and can create tools to reconstruct the memory into a proper filesystem image.
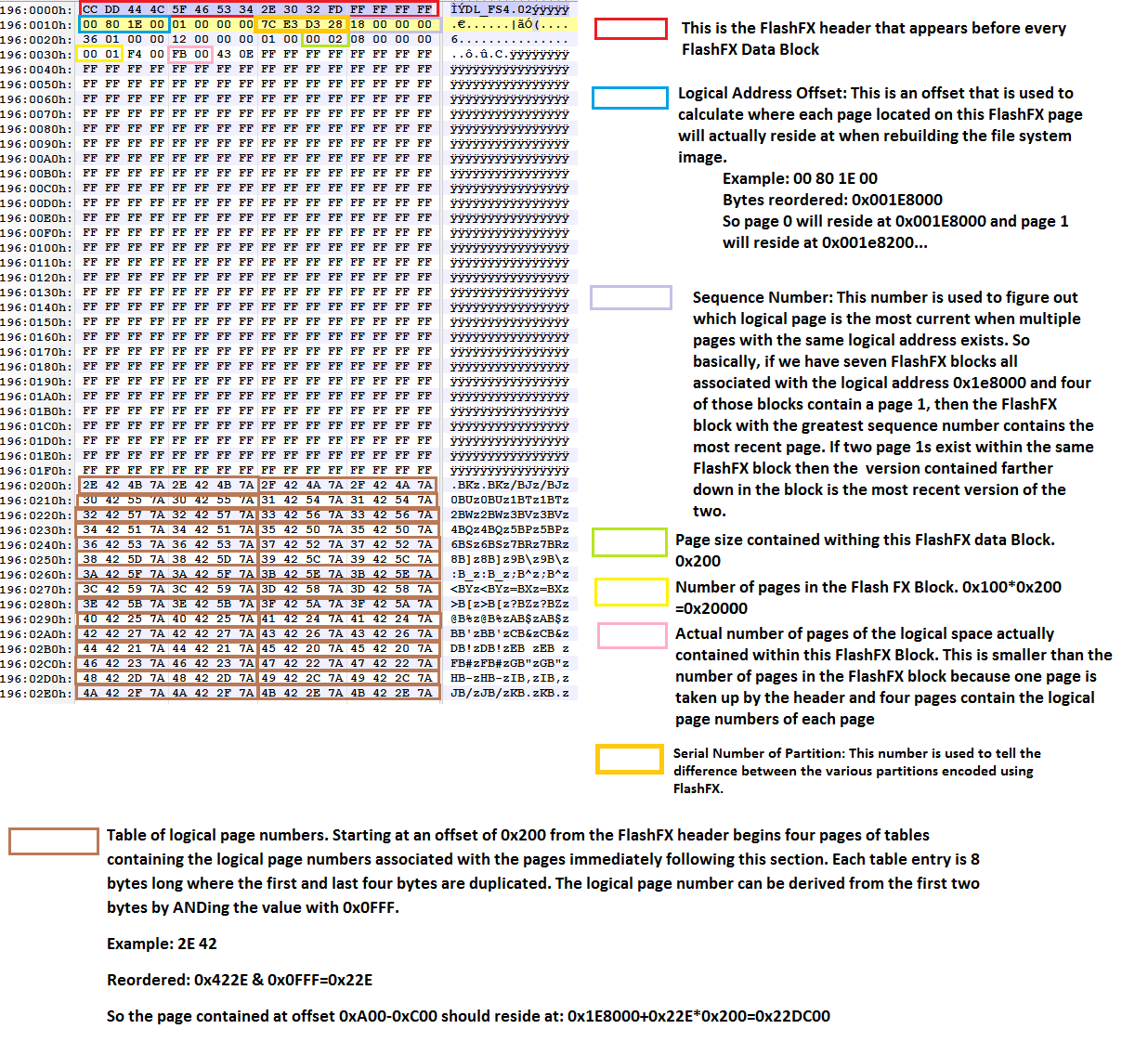
Figure 6: Raw reads from NOR and NAND flash memory must first be reordered before the filesystem can be correctly read.